| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
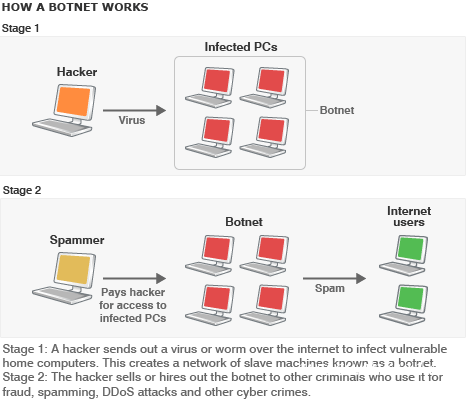
Almost two million PCs globally, including machines inside UK and US government departments, have been taken over by malicious1 hackers2. 包括英国和美国政府部门在内的全球将近200万的电脑被黑客恶意攻击。 Security experts Finjan traced the giant network of remotely-controlled PCs, called a botnet(僵尸网络), back to a gang of cyber criminals in the Ukraine. Several PCs inside six UK government bodies were compromised by the botnet. Finjan has contacted the Metropolitan3 Police with details of the government PCs and it is now investigating. A spokesman for the Cabinet Office, which is charged with setting standards for the use of information technology across government, said it would not comment on specific attacks "for security reasons". "It is Government policy neither to confirm nor deny if an individual organisation4 has been the subject of an attack nor to speculate(思索,推测) on the origins or success of such attacks." He added: "We constantly monitor new and existing risks and work to minimise their impact by alerting departments and giving them advice and guidance on dealing5 with the threat." How does a botnet work? It is the second time in a year that PCs inside government departments have been hacked6 to form part of a botnet. On this occasion, the machines were infected with software which allowed them to be taken over and enslaved in the botnet due to vulnerabilities(脆弱点) in web browsers7. PCs inside a botnet can be forced to carry out instructions At the mercy Once a machine has been compromised, it can be instructed to download further software, which puts the machine at the mercy of malicious hackers. The compromised PCs are capable of reading e-mail addresses, copying files, recording8 keystrokes, sending spam and capturing screen shots. Once a single machine inside a corporate9 network has been made part of the botnet it puts other machines on the network at risk. The Cabinet Office would not give details of what the compromised machines had been instructed to do, nor the names of the different government departments that had been infiltrated(浸润,渗透). The cyber criminals, who have not been caught, were selling access to the compromised machines, thought to be mainly PCs inside companies, on a hackers' forum10 in Russia. One thousand machines were being sold at a time for between $50 and $100. Finjan reports that the botnet is under the control of six criminals who are able to remotely control the infected machines. Different organisations Almost half of the infected machines were in the US. Six percent of the botnet, about 114,000 machines from 52 different organisations, were from the UK, among them a single PC inside the BBC's network. Many of the infected machines will have been caught by routine information security policies at firms, as it was in the case of the BBC, but Finjan says many of the botnet PCs are still active. More than 70 different national government agencies from around the world were caught up in the malicious network. Yuval Ben-Itzhak, chief technology officer for Finjan, told BBC News: "When we looked at the network domain11 names to see where the [compromised PCs] come from we were surprised to see many government networks, including UK government computers. "Obviously we reported it and they have now dealt with it. There were six UK agencies with at least one computer in each department that was running the bot. "I'm not at liberty to name the actual agencies - but this isn't a unique story to the UK, they were running in many other non-UK, government bodies too." Government bodies A number of different government bodies are responsible for IT security and deployment12 across the UK. They include the Central Sponsor for Information Assurance, the National Technical Authority for Information Assurance, and the the Centre for the Protection of National Infrastructure13 (CPNI), the government body which is part of the British Security Service and responsible for providing security advice to organisations that make up critical services in the UK. All of the infected machines were Windows-based PCs and the vulnerability(弱点,漏洞) was targeting security holes in Internet Explorer and Firefox. Mr Ben-Itzhak said: "What is unique is the number the size of the network. When we look at a similar network last year they were in the hundreds of thousands. Now were looking at mega-size botnets." In contact A spokeswoman for the Metropolitan Police said: "This is an ongoing14 investigation15. We are aware of this botnet and are taking appropriate action." Large botnets can be used to co-ordinate attacks to knock parts of the network, or specific websites, offline, called a Distributed Denial of Service attack. Last year, the CPNI told a Cabinet Office-commissioned independent review that stopping such attacks was difficult. It said: "The attacks are relatively16 low in sophistication(诡辩,强词夺理), but have been highly effective due to the large number of compromised machines involved. "It is difficult to defend against a sophisticated Distributed Denial of Service attack without impacting legitimate17 business use." The CPNI recommended that the best defence against these attacks was appropriate monitoring of the network. 点击  收听单词发音 收听单词发音
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
- 发表评论
-
- 最新评论 进入详细评论页>>